Data Storage, Transmission and Cloud Services Policy Info
General Statement
All data that the University and its employees are charged with stewarding should be accounted for, access authorized and be available for third party audit.
IWU is bound by federal laws that concern constituent data such as HIPAA, FERPA, GLBA as well as new privacy laws recently enacted. These laws require IWU to handle data in a certain manner. Failure could lead to penalties, fines and reputation consequences.
What does this policy accomplish?
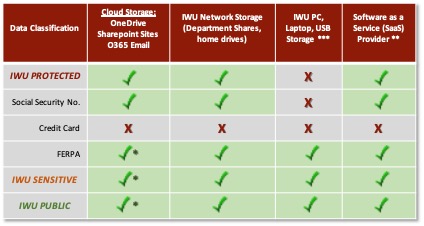
- Defines acceptable storage services that can be monitored and controlled not only for the safety of our constituent data but also to comply with regulatory laws and information security frameworks.
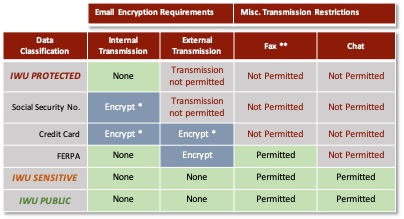
- Simplifies usage – WHERE to store data – how employees can TRANSMIT certain classifications of data. (i.e. What data should be encrypted via email)
- Provides steps to ensure that any cloud services, outside of file storage, [i.e. Civitas, Qualtrics, Softdocs] are properly reviewed from a data security perspective and documented prior to contract sign off.
- Ultimate goal – Simplify, protect and centralize the administration of all IWU data.
How do I know if I am in compliance?
- The policy clearly defines acceptable methods to store data. If you are currently storing any IWU data that falls within the tiers defined in the Data Classification Policy, within an approved platform, you are all good!
- If you are storing data in an area shown as not approved, please fill out the Cloud Application Review Request and Client Engagement Services will be in contact with you to run though a brief review process.
- If you are transmitting data in a manner contrary to the policy please follow the same review process.
How does this apply to cloud services like file storage or apps that my department wants to/or is using currently?
The policy was created to ensure that any new cloud services go through a vetting process to ensure that the vendor application that any IWU department or college wishes to utilize is adhering to the appropriate security controls to protect all IWU data. In addition, at the time of this policies approval, IWU is aware that some cloud applications within the University may not have gone through this process. It is critical that if a cloud application was not subjected to review, by CES and the ISO, prior to contract signing that those applications be identified. That is where the Cloud Application Review Request comes in.
What if I ignore the policy?
This policy has taken over six months to generate, revise and walk through with each university cabinet for discussion. The risk of not adhering to the policy could, depending on the data type, lead to serious financial or reputation consequences if that data is breached or disclosed.
What are my next steps?
- If you are storing data outside of the approved platforms stated within the policy OR transmitting data outside of the parameters defined then please fill out the Cloud Application Review Request form.
- Once completed, CES and the ISO will review completed form and get back to you with next steps. This may involve a meeting, brief phone conversation or a simple acknowledgement that no action is required.
- If action is required IT will work with you to move the data or adapt the current platform to allow for the appropriate security controls to be put in place.