Crowdstrike - File Alert Investigation _ Exemption Procedure
Summary
The Crowdstrike Endpoint Detection and Protection platform can identify and alert designated IWU security administrators about potentially malicious files. It is the responsibility of these security admins to thoroughly investigate each alert and determine if it is a true positive or false positive. Since the security admins are not subject matter experts (SMEs) for all applications on server or employee endpoint systems, additional investigation by the IT Support Configuration Management team or the IWU Enterprise Systems teams may be necessary.
This procedure outlines the steps to be followed in evaluating any file alerts detected by Crowdstrike and specifies the actions required from the relevant teams.
It is required to address and resolve alerts promptly to avoid negatively impacting the productivity of servers or employees.
Procedure
When an alert is received by the security admins it should be logged in Smartsheet for future reference. Crowdstrike only keeps incidents logged for 90 days so it is important to track these for future reference if needed.
The Smartsheet can be found here: Crowdstrike File Detections _ Tracking Exemptions
STEPS
- Alert received by Crowdstrike
- Email sent to IWU Security Admins for review
- Alert is reviewed on the Endpoint Detections Dashboard (Security Admin (SA) / CISO)
- If the alert is determined to be a TRUE positive the information does not need to be logged. The goal is to only log FALSE positives.
- If the alert is a true positive the SA and CISO will follow a separate procedure for remediation otherwise continue with the remaining steps below.
- The information is logged into the Smartsheet (Security Admin / CISO)
- If the SA or CISO can determine if an exemption can be made then they can proceed and ensuring the appropriate Smartsheet columns are noted. (Security Admin / CISO)
- If the file cannot be clearly determined an email should go out to the following depending on the operating system:
- Endpoints - Windows 10,11 etc., MAC - Kyle.Lewis@indwes.edu, anthony.williams@indwes.edu, nate.woordard@indwes.edu, paul.delavergne@indwes.edu
- Server Systems - josh.richardson@indwes.edu (Josh can then follow up with the enterprise applications group or application owner [CC: SA and CISO] for discernment. The backup would be michael.raver@indwes.edu
- Once a final determination is made the app owner will email the SA and CISO. A block will remain or exemption will then be applied.
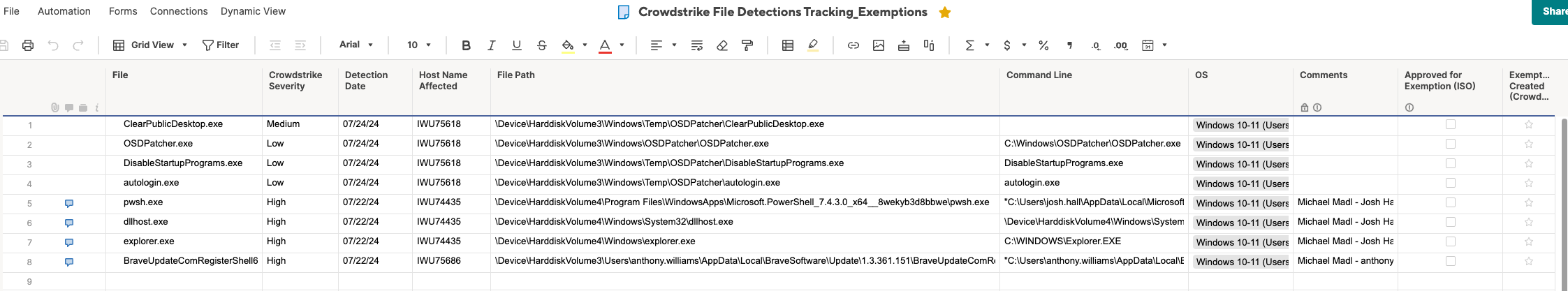
Column Information (required fields) (Security Admin / CISO)
- File - Cut paste the file name that was detected
- Crowdstrike Severity - Note the alerted severity of the event as indicated by the console alert
- Detection Date - First date identified
- Host Name Affected
- File Path
- Command Line
- OS
- Comments - Note anything relevant in the comments (i.e. - user affected)
- Approved for Exemption (ISO) - This will be filled out by either the security admin or CISO upon completion of the investigation
- Exemption Created - Checking off when the exemption has been entered into the console by the security admin or CISO
